Company Overview
DataVigilant InfoTech is an Information Technology product and services company, established in the year 2014 by professionals with a cumulative experience of over 30 years in the field of Information Technology.
DataVigilant aims to address the basic need of its customers, of a reliable guardian for their computing environment.
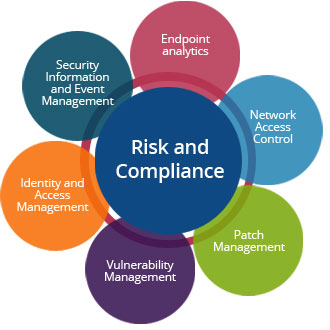
DataVigilant wishes to give the industry a never before experience of a secure and worry free compute. The company intends to provide solutions based on the Risks associated with the business of its customers.
DataVigilant believes in setting high standards for the services provided to its customers, and believes in giving its customers the best of value for their investments. The company understands that always ON and prompt response is the key to customer satisfaction.
As the saying goes “A stitch in time saves nine” so is the companies approach for any customer being served – PROACTIVE is the BUZZWORD.
Leadership
Mr. Santosh Zapdekar
Founder
With an experience of over 12 years in the field of Information Security, he is responsible for the overall operations of DataVigilant & also heads the sales division of the company. He is a visionary & believes in maintaining outstanding customer relationship.
Mr. Prabhit Nair
Co-Founder
With over 14 years of experience in the field of information security, he heads the technical division of the company and is responsible for technical services delivery. He has excellent problem solving capabilities & very good team management skills.
Our Values
Probity
We give utmost importance to honesty and integrity in our business practices.
Teamwork
We Align and blend strengths of individuals so that they complement each other and deliver the best output.
Ethics
We ensure, our business practices are in accordance with the rules or standards for right conduct or practice.
Transparency
We believe in transparent dealings with our employees and customers alike. Transparency builds trust.
Commitment
We stay devoted to the promises made, and exceed customer expectations.
Quality
We make every effort to maintain high standards in services & solutions offered to our customers.
Vision and Mission
Vision
To be a growth oriented company with firm commitment of caring for quality products and services.
Customer is at the heart of our business values, operations and ideas. With customer centric approach we see our company among the top Information Technology service providers in the Industry.
Mission
Information Technology is evolving at a very rapid pace and so is the need for a proactive and efficient service provider, DataVigilant will provide highly skilled technical team and flawless Project Management capabilities to address the challenges posed by the fast evolving Information technology and Information security arena.


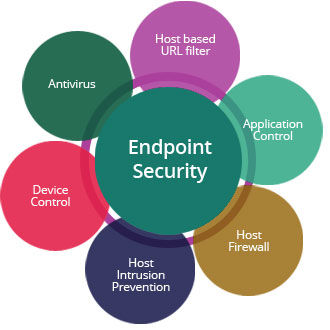
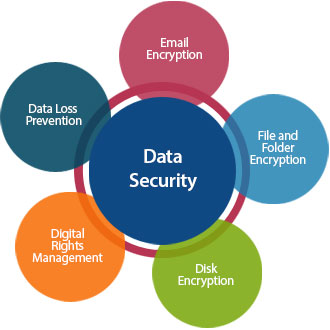
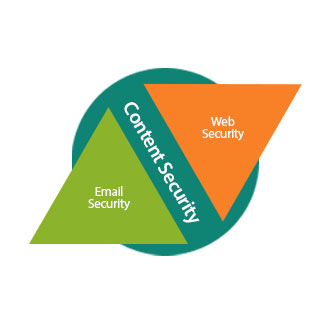
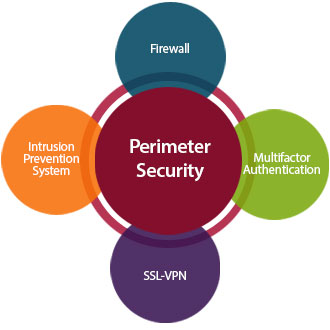











 For Business Enquires
For Business Enquires